What Is a Honeypot in Cybersecurity?
Honeypots, a highly advantageous technique, empower IT teams to effectively counter and outsmart potential of Hackers. A honeypot involves simulating an IT system or software application, designed as enticing bait to lure the focus of attackers. Despite presenting itself as a genuine target, the honeypot is, in reality, counterfeit, meticulously supervised by the IT security team. Derived from the notion that this ruse acts as a “sweet” trap for attackers, the term “honeypot” harks back to the age-old adage “You catch more flies with honey than with vinegar.”
Purpose of a Honeypot in Cybersecurity
In cybersecurity, honeypots serve multiple purposes:
- Distraction: Honeypots act as a strategic diversion for attackers, consuming their time and efforts that could otherwise be directed at actual targets. The attention drawn to honeypots reduces the resources attackers allocate to real attacks.
- Threat Intelligence: By duping malicious actors into engaging with honeypots, organizations gain insights into their attack techniques and tools. Monitoring attacker behavior within honeypots enhances IT teams’ comprehension of these attacks, aiding in effective defense strategies.
- Research and Training: Honeypots provide a controlled environment for IT professionals and students to conduct research and training activities. Serving as a secure arena, honeypots facilitate observation and analysis of diverse cyberattack types.
What Are the Different Types of Honeypots?
Honeypots come in various forms and sizes, tailored to the specific attack types of interest to IT teams. Here are a few essential honeypot types to familiarize yourself with:
- Email Traps: An email trap serves as a honeypot aimed at gathering spam and malicious emails. IT teams establish a fictitious, publicly accessible email address that exposes cybercriminals. Messages directed to this address can be promptly marked as potential spam or harmful content.
- Decoy Databases: Decoy databases function as honeypots that present counterfeit data to attackers, enticing and confusing them during an attack. While the contents of such a database may resemble genuine information, they are essentially useless or potentially damaging to the intruder. This diversion keeps attackers from uncovering genuine, valuable data.
- Malware Honeypots: A malware honeypot is a specialized decoy designed to ensnare malicious software by simulating a vulnerable system or network, like a web server. This honeypot intentionally incorporates security vulnerabilities that attract malware attacks. The collected malware can be analyzed by IT teams to comprehend its actions and trace its source.
- Spider Honeypots: Spider honeypots are devised for software that explores the web, often referred to as “spiders.” IT professionals create fabricated websites or pages susceptible to internet-based assaults like SQL injection and cross-site scripting (XSS). These vulnerabilities attract malevolent automated programs that scour websites for weaknesses, searching for potential targets.
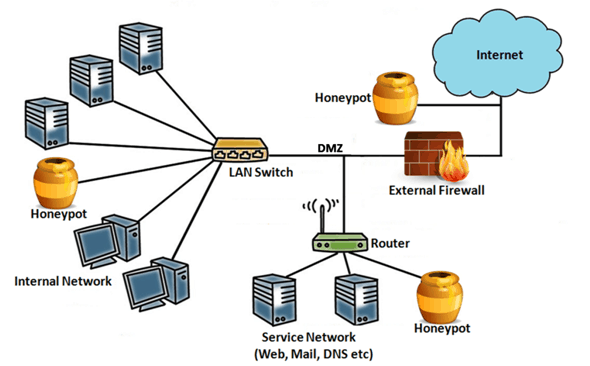
Security Interaction of Honeypots
- High-Interaction Honeypots: These honeypots replicate fully operational systems, faithfully imitating authentic IT devices or applications. As the name suggests, they allow attackers to engage with them as if they were genuine entities, affording complete privileges and access. While high-interaction honeypots yield extensive insights into attackers’ methods, they necessitate intricate setup and ongoing maintenance due to their complexity.
- Low-Interaction Honeypots: Conversely, low-interaction honeypots emulate specific segments of IT environments, implementing only select applications or services. These honeypots grant attackers a restricted array of interactions. Consequently, low-interaction honeypots are simpler to create, demand fewer resources, yet offer a reduced level of realism and information.
Physical vs. Virtual Honeypots
- Physical Honeypots: As the name implies, physical honeypots are tangible IT devices or systems linked to a network, each possessing its distinct IP address. While they offer enhanced realism, their usage is less prevalent due to the associated expenses.
- Virtual Honeypots: Conversely, virtual honeypots emulate operating systems or applications within virtual machines. This approach facilitates rapid deployment and creation of new honeypots. However, it lacks the ability to capture attacks targeting physical vulnerabilities.
Advantages and Disadvantages of Honeypots
Advantages:
- Early Detection of Attacks: Honeypots offer the advantage of promptly identifying novel or previously undiscovered cyberattacks, enabling rapid and efficient responses from IT security teams.
- Wasted Time and Effort: Honeypots can divert attackers’ attention towards an imitation target, causing them to expend their time and efforts on a nonproductive pursuit, thereby mitigating real threats.
Disadvantages:
- Attracting Excessive Attention: The revelation that attackers have been ensnared by a honeypot might lead them to retaliate by intensifying their assaults on the organization’s legitimate systems, potentially escalating the overall risk.
- Resource-Intensive: Honeypots demand substantial resources and specialized knowledge for proper setup and maintenance, which could result in a relatively low return on investment compared to other cybersecurity measures.
Best Practices for Implementing Honeypots
Here are some best practices for implementing honeypots in cybersecurity:
- Proper Configuration and Maintenance: Ensure honeypots are configured accurately and undergo consistent maintenance to retain their allure as targets for attackers.
- Integration with Other Security Systems: Honeypots yield optimal results when seamlessly integrated into the broader spectrum of IT security tools and protocols.
- Regular Monitoring: Maintain vigilant oversight of honeypots to promptly detect any ongoing attacks, enabling timely responses from the IT security team.
Applications of Honeypots in the Real-World
Below are several real-world scenarios showcasing the application of honeypots in cybersecurity:
Government and Military: Honeypots play a pivotal role in governmental and military contexts by diverting assailants away from high-value targets. These deceptive systems safeguard critical infrastructure like power grids and communication networks.
Financial Industry: Given their prominence as prime targets, financial institutions leverage honeypots effectively. These institutions utilize honeypots to uncover fraudulent financial activities and thwart endeavors to pilfer customer data.
Intellectual Property Protection: Enterprises seeking to safeguard their intellectual property (IP) employ honeypots to confound and confine potential attackers, thereby safeguarding valuable IP assets.
Don’t forget to check out our latest Blog – Sim Box Fraud

